How the NSA obtains and uses airline reservations
A front-page report in today’s New York Times based on documents leaked by NSA whistleblower Edward Snowden confirms that the NSA, like the DHS, uses airline reservation data as part of its profiling and social network analysis of US citizens and foreigners. Today’s report also raises new questions, and suggests some answers, as to how the NSA obtains and uses this airline data.
The Times’ report today on NSA social network analysis mentions that:
The [NSA] can augment the communications data with material from public, commercial and other sources, including … passenger manifests…, according to the documents. They do not indicate any restrictions on the use of such “enrichment” data, and several former senior Obama administration officials said the agency drew on it for both Americans and foreigners….
[T]he N.S.A. correlates 164 “relationship types” to build social networks and what the agency calls “community of interest” profiles, using queries like “travelsWith“.
In their most basic form, passenger manifests list each passenger individually and do not indicate which passengers were traveling together. At a minimum, either “Advance Passenger Information” (API) data, some other source of “enhanced” passenger manifest data, or complete Passenger Name Records (PNRs) would be needed to identify which passengers on a given flight had reservations in the same PNR (a single PNR can contain the reservations for an entire party or group traveling together) and thus who “travelsWith” whom.
We’ve long known that the DHS collects API and PNR data about US citizens and foreigners alike, compiles this data in its Automated Targeting System and Secure Flight databases, and mines this data both to target individuals (including journalists and activists) and for social network analysis (correlating e.g. telephone numbers and airline reservations) to identify and target new suspects on the basis of their association with current suspects (i.e. as a suspicion-generating or guilt-by-association system).
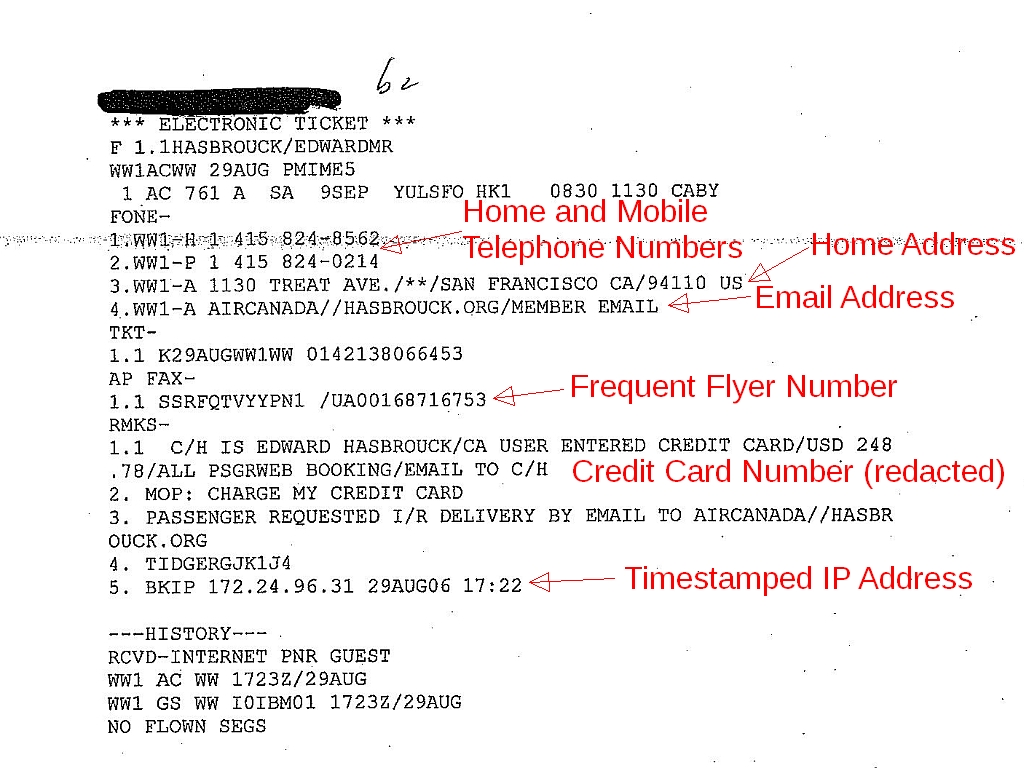
A typical PNR like the one shown above (from a DHS Automated Targeting System dossier; click the thumbnail for a larger image) includes a timestamped IP address (line 5 of the “remarks” in the example above), email address, home address, credit card number, mobile phone number, etc., so it can readily be correlated with Internet, communications, and financial records.
The NSA would presumably have been interested in flights worldwide, including flights within parts of the world far from the USA, while the DHS claims to collect PNR data only for flights to, from, within, or via the US. But we know that the DHS can, and sometimes does, collect PNR data about flights elsewhere.
As we reported in 2007, and as was mentioned in a front-page story in the Washington Post based on our research, ATS records released by DHS in response to our requests (you can request your own ATS file using the forms here) confirmed that the DHS already had “root” access to the computerized reservation systems (CRSs), so that the DHS could retrieve any PNR in those CRSs, even if it didn’t include any US flights.
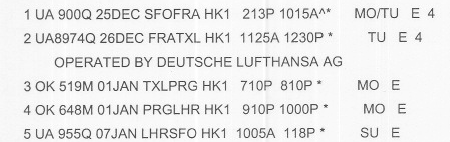
The “smoking gun” confirming DHS root access to CRSs was this PNR for someone who traveled from San Francisco to Berlin (TXL) on United Airlines and a United/Lufthansa codeshare flight, stayed in Berlin for six days, continued from Berlin to London (LHR), stayed in London for another six days, and then returned to SFO on United:
The portion of the journey from Berlin to London via Prague was on Czech Airlines (OK), an airline which does not (and did not then) fly to, from, or via any point in the US. Additional details in the PNR showed that a separate ticket was issued for the OK flights, which did not connect to flights to or from the US. A CRS user with a United Airlines user ID and privileges would not have been able to see these flights. Only a user with an ID from the travel agency that made these reservations, or a user with “root” privileges (such as a user with an ID from the CRS company), would have been able to see all of the data that the DHS was able to see and import into ATS.
So could the NSA have obtained its copies of PNR and/or API data from DHS, or by using the root-user credentials that CRS companies had provided to the DHS? Maybe. Since neither DHS nor the CRSs keep logs of who accesses their respective copies of PNR data, there’s no way to know for sure except through leaks or the testimony of whistleblowers.
But we suspect that the NSA has some way to obtain PNR and/or API data independent of the DHS.
According to our CRS sources, DHS user IDs have been used to retrieve PNRs — sometimes the PNRs of every passenger on a flight — for flights within other parts of the world, far from the US. But this appears to have been done only on a case-by-case basis, for specific flights. Retrieving all worldwide PNRs through the sort of access available with the CRS user credentials that we believe to have been made available to DHS, even with root user privileges, could place costly and problematic burdens on CRS server resources.
The NSA may have gotten copies of the API and/or PNR data the DHS systematically pulls from the CRSs for flights to, from, or via the US. But for flights in the rest of the world, it would have been more convenient and cheaper for both the NSA and the CRSs to set up systems to “mirror” CRS data, similar to the systems set up by the NSA to obtain mirror copies of telephone and Internet traffic and metadata.
Hacking the CRSs, or the exceptional airlines that don’t outsource hosting of their PNRs, as the NSA was recently reported to have done, would logically have been reserved for those few travel IT companies that didn’t cooperate with the NSA’s “requests” for real-time mirroring of their hosted PNR databases.
Would airlines or CRSs “voluntarily” have given the NSA root access to PNRs? Almost certainly, yes.
Unlike telephone and Internet companies, at least some of which have challenged DHS and NSA demands for wholesale data dumps and pervasive real-time dataveillance of their customers, there is no indication that any airline, CRS, or travel IT company — in the US or abroad — has ever said no to any government request or challenged a government demand for passenger data. As early as 2002, CRSs were giving PNR data to TSA contractors to test automated profiling systems (precursors of today’s Secure Flight and ATS), without telling even the airlines what they were doing. CRSs have even tried to sell PNR data to competing airlines — again without telling the airlines, much less the passengers, to which the PNRs pertained.
If practices like this were the norm, why would CRSs have drawn the line at cooperation with the NSA?
Would this have been legal? Maybe, at least with respect to US law, and more likely legal than the NSA’s collection and use of communications data and metadata.
Government restrictions on, or surveillance of, travel are subject to strict scrutiny, and in the absence of narrowly-defined necessity are prohibited by both the First Amendment to the US Constitution and Article 12 of the International Covenant on Civil and Political Rights.
But as we’ve noted previously, if you ignore the applicable provisions of the US Constitution and international treaties, US law provides less protection for data about the movements of your physical body than for data about the movements of your messages. This is wrong, and contrary to people’s reasonable expectations of privacy, but Congress seems unlikely to fix this legal anomaly.
Much of the debate about the NSA’s telecommunications and Internet surveillance has concerned whether it violated laws on wiretapping or unauthorized disclosure of communications records. There are no comparable US laws protecting travel records. Under the “third party doctrine”, API and PNR data is considered the sole property of travel companies. Airlines, CRSs, travel agencies, and other travel companies may quibble over which of them own the information they hold about our travels. But under US law, we have no legal interest in this information about us. It can legally be used, sold, or disclosed, including to government agencies in the US or anywhere else in the world, without our knowledge or consent.
Privacy policies of US airlines, CRSs, and other travel companies typically allow those companies to disclose personal information to third parties whenever it is “requested” by any government agency (not just when it is “required”). Government agencies can legally obtain this data for the asking, without the need to issue a mandatory order or to have a legal basis to issue such an order.
Airlines and CRSs that operate in other countries, particularly in Canada or the European Union, probably violated (and are continuing to violate) those countries’ laws either by allowing the NSA to access data about their customers, or by outsourcing storage of their data (including data collected for them by their agents) to companies in the US that can allow access by the NSA or other third parties without the airlines’ knowledge. Both Canadian and EU laws require these companies to be able to provide an accounting of third-party disclosures on request, but the absence of CRS access logs makes compliance with these laws impossible.
The EU-US PNR agreement allows airlines to transfer some passenger data to the DHS. (In July 2013, the European Parliament voted to recommend that the EU “give consideration to … the possible suspension of the passenger name record (PNR) … agreement[]” in light of the NSA’s surveillance of EU citizens,) But that agreement does not protect airlines, CRSs, or other travel companies against liability for violating EU laws by transferring passenger data to the NSA, or –perhaps more importantly — for outsourcing hosting of personal data to US-based CRSs that do not, and under US law cannot, provide adequate protection for that data once it is on their servers in the US. US-based, EU-based, and third-country airlines and CRSs are violating EU law.
The NSA itself may have violated the Privacy Act, in two ways.
First, NSA officials may have committed criminal violations of the Privacy Act by operating a system of records containing information about “US persons” without the NSA first having published a proper notice of the existence of the system, the categories of individuals about whom it includes information (including US citizens who are not suspected of, or under investigation for, any offense), the types of information contained in the system, the ways that information is stored in and retrieved from the system, and the ways that information from the system is used and disclosed. Operating such a system of records without proper prior notice to the public is a crime only Federal agency officials can commit, and for which none of them are ever prosecuted. But we shouldn’t forget that the responsible NSA officials are, in all probability, criminals.
While this is a criminal offense, it can also be the basis for a civil action under Section (g)(1)(d) of the Privacy Act, if the failure to comply with the notice requirement “has an adverse affect on an individual”.
Second, the NSA (like the DHS) may have violated the Privacy Act by keeping records of how individuals exercise rights protected by the First Amendment without express statutory authorization and when those records are not “pertinent to and within the scope of an authorized law enforcement activity”. The social network records constructed by the NSA would appear to be, per se, records of how individuals exercise the “right of the people … peaceably to assemble”, as protected by the First Amendment. That gives affected individuals, particularly those whose exercise of First Amendment rights is chilled, cause for civil actions.
We would welcome any information from readers about how the NSA obtains and uses travel data.
[…] Indiz für “root access” des DHS auf Passagierdaten (veröffentlicht von Edward Hasbrouck). Verfügt die NSA ebenfalls über einen Exklusivzugang? […]
Pingback: NSA Storing Internet Data, Social Networking Data, on Pretty Much Everybody
Pingback: Security Expert: “The Details Matter Less and Less. We Have To Assume That The NSA Has EVERYONE Who Uses Electronic Communications Under CONSTANT Surveillance” — State of Globe
Pingback: Security Expert: The NSA Has EVERYONE Under CONSTANT Surveillance | Thought FTW
Pingback: wchildblog | Security Expert: “The Details Matter Less and Less. We Have To Assume That The NSA Has EVERYONE Who Uses Electronic Communications Under CONSTANT Surveillance”
Pingback: The Progressive Mind » Security Expert: “We Have To Assume That The NSA Has EVERYONE Who Uses Electronic Communications Under CONSTANT Surveillance” | Washington’s Blog
Pingback: Papers, Please! » Blog Archive » TSA’s lying “response” to today’s story in the New York Times
Pingback: Security Checks Start Long Before You Fly: TSA Accessing Government and Private Databases to Pre-Screen Everyone | LeakSource
Pingback: Glenn Greenwald Says NSA, GCHQ Dismayed They Don’t Have Access to In-Flight Internet Communication |
Pingback: Two Administrations and Congress Dismantled the Constitution – How Can It Be Restored? | From the Trenches World Report
Pingback: Papers, Please! » Blog Archive » US government veterans call for curbs on surveillance
Pingback: The American Panopticon: Why A Free Society Can’t Have Mass Surveillance - Government Denies Knowledge
Pingback: “KOSTENLOSES W-LAN IST SEHR SEHR TEUER”: SNOWDEN | subito
Note that in addition to the NSA and DHS, the FBI also obtains copies of airline reservations from commercial travel industry intermediaries.
We wrote about this in 2009:
https://papersplease.org/wp/2009/09/28/fbi-wants-records-from-travel-data-aggregators/
And The Intercept published leaked documents in 2017 confirming this:
https://theintercept.com/2017/01/31/based-on-a-vague-tip-the-feds-can-surveil-anyone/
Pingback: Intermezzo (840) | Blue Archive
“Espionage, Spying and Big Corporate Data, These Are a Few of China’s Favorite Things” (by Neal Dennis, Arbor Networks, August 17, 2015):
https://www.arbornetworks.com/blog/asert/espionage-spying-and-big-corporate-data-these-are-a-few-of-chinas-favorite-things/
Pingback: Will “continuous vetting” include new demands for travel information? | Papers, Please!
Pingback: Volume 16, Number 18 – 9/30/13 – The Arlington Institute